The Ultimate Guide to Phishing
2025 edition
Overview
Generally associated with unsolicited emails sent by a hacker to a wide range of targets, phishing is a ‘bait and switch’ tactic designed to trick targets into revealing personal information such as passwords or credit card details. The phishing email purports to be from a known party such as a bank or a colleague and requests a response which can include redirection to a spoof website where (for example) the target is encouraged to bank usernames or passwords. Phishing is a form of social engineering.
Analyst reports

AV-TEST on DevOps
Kaspersky tops 2024 security tests with record 97% TOP3...
Last week

Gartner on SaaS
Palo Alto Networks invests in Asia-Pacific cloud securi...
Last month

Gartner on Malware
AI to halve time needed for account takeover by 2027
Last month

Gartner on Advanced Persistent Threat Protection
Exclusive: SquareX aims to redefine cybersecurity with ...
Thu, 27th Feb 2025

IDC MarketScape on Malware
Sophos MDR services protect 26,000 organisations global...
Tue, 14th Jan 2025
Expert columns

By Rakesh Prabhakar of Zoho
How can small and medium businesses safeguard against r...
Last week
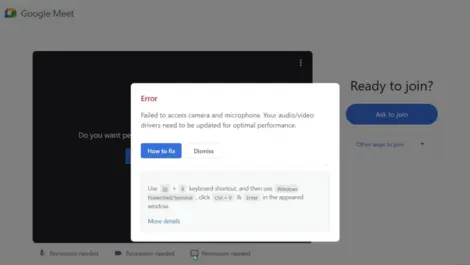
By Dakshitaa Babu of SquareX
Why ClickFix attacks are outpacing enterprise security
Last month

By Jack Meltzer of Gallagher Security
Building a culture of cyber hygiene
Last month

By Bob Gilbert of Netskope
Bad AI, good AI: harnessing AI for a stronger security ...
Last month

By Matt Caffrey of Barracuda Networks
Why email security needs automated incident response
Fri, 21st Feb 2025
Interviews

Discussing Cloud Services
Exclusive: Why every day should be World Backup Day
This month

Discussing Multi-factor authentication
Exclusive: Yubico pushes for wider protection under Aus...
Last month

Discussing Malware
Exclusive: Infoblox reveals the importance of DNS secur...
Fri, 21st Feb 2025

Discussing Firewalls
Exclusive: Radware SVP Travis Volk discusses evolving c...
Tue, 10th Dec 2024

Discussing Collaboration
Exclusive: Qualys MD discusses cybersecurity in ANZ reg...
Wed, 4th Dec 2024
More expert columns

By Jason Whyte of Trustwave
How to outsmart ransomware and build resilience within ...
Wed, 12th Feb 2025

By Johan Fantenberg of Ping Identity
How A Passwordless Future Can Become A Reality
Thu, 30th Jan 2025

By Yubico
Cybersecurity in 2025: Insights and predictions from Yu...
Thu, 16th Jan 2025

By Jake King of Elastic Security
Elastic Security's top three cybersecurity predictions ...
Tue, 17th Dec 2024

By Sneha Banerjee of ManageEngine
Sneaky scams to watch for this holiday season (and how ...
Fri, 13th Dec 2024

By Curtis Raams of Prvidr
Countering the security threat from within
Thu, 12th Dec 2024
Recent news

About Elections
Australians warned of rising election scams as poll nea...
Last week

About Malware
Identity Digital teams up with Shadowserver to fight cy...
Last week

About Ransomware
Australian firms move to passkeys as cyber threats bypa...
Last week

About Online fraud
AI-powered scams surge online as Microsoft blocks USD $...
Last week

About Collaboration
Trend Micro explores Russian cyber underground's influe...
Last week
More news

About Cloud Services
N-able integrates Adlumin for Microsoft 365 breach prev...
This month

About Ransomware
Report explores Russian cyber underground's global impa...
This month

About Ransomware
AI amplifies cyber threat; non-human identities at risk
This month

About Malware
New Netflix series 'Adolescence' sparks safety debate
This month

About Social Media
Rising threats to influencers as cyber attacks escalate
This month
Even more news

About Ransomware
Fast Flux DNS tactics escalate cyber defence challenges
This month

About Software Updates
Kaspersky discovers & patches zero-day Chrome flaw
This month

About Scams
Scams cost Australian small businesses AUD $7.9 million
This month

About Data Protection
Jared Siddle warns of risks in business AI tool usage
This month

About Cloud Services
Evolving strategies essential amidst AI-driven cyber th...
This month
Other guides
You can read other related guides from Email Security, Cybersecurity, Breach Prevention, Advanced Persistent Threat Protection, and Artificial Intelligence.
Powered by

